Learnings from the Industry Targeted Cyber Attack Statistics of 2024
Dr Shekhar Pawar elaborates on the importance of cybersecurity for enterprises to protect their business, reputation, finance, and growth in the new year.

This article with historical data from the year 2024 helps in recognising patterns in cyber attacks. Threat actors often reuse infrastructure, such as IP addresses and domains, across multiple campaigns. By analysing past data, security teams can uncover these patterns and predict future attacks.
In 2024, cybersecurity has seen significant improvements, with advancements in artificial intelligence (AI) and machine learning (ML) technologies enabling real-time threat identification and mitigation. This has improved efficiency in detecting anomalies and responding to cyber threats. Global collaboration has led to a decrease in large-scale cyberattacks such as ransomware. Public awareness and education about cybersecurity have increased in many countries, with more individuals and organisations adopting strong security practices like regular software updates, multi-factor authentication, and regular cybersecurity awareness training. New laws and regulations have been enacted to enhance cybersecurity standards and protect critical infrastructure. Quantum cryptography, a promising technology, is expected to revolutionise data security in the coming years.
Even though technological advancements and collaboration are improving the cybersecurity of industries in many countries, it is also evident that the effective uses of AI technologies are being used by cybercriminals for more sophisticated cyberattacks. The SecureClaw Cyber Threat Advisory team studied more than 5000 international cyber attack news stories in various industries and created a most visible cyber threats trend considering sampling basis summary report, which will be discussed in this article. It is worth noting down that many organisations never report the cyber incident to the media or government; hence, no one is able to identify exact statistics of the cyber attack trends. Few countries have strict enforcement of data privacy and other acts, where many organisations are forced to report cyber incidents to the government or even to the media. This article is an attempt to check the pulse of the cyber attack trends using whatever was evident via various sources of the cyber attack news. It is showing a diagrammatic representation of the USA's industry-specific cyberattacks of the year 2024, as well as another diagram showing worldwide ransomware attacks of the year 2024.
Overview of Malware Attacks
Malware means ‘malicious software’ and refers to any software intentionally designed to cause harm to the confidentiality, integrity, or availability of any computer, server, client, OT, IoT, or network. Common types of malware include viruses, worms, trojans, ransomware, spyware, adware, and rootkits. Malware can infiltrate systems through various methods such as phishing emails, infected files, malicious websites, or exploiting software vulnerabilities. Once installed in a system, malware can steal, encrypt, or delete data. It can hijack core functions or even spy on user activity. It can even lock users out of their devices until a ransom is paid while working with a ransomware attack. Cybercriminals use malware for financial gain, data theft, espionage, or simply to cause disruption in the operations.
The cShell DDoS malware was recently discovered in December 2024. It targets poorly managed Linux SSH servers by exploiting weak SSH credentials and using Linux tools like screen and hping3 to execute sophisticated DDoS attacks. The error messages during the malware's installation process are written in German, suggesting a possible origin or operational clue.
The HiatusRAT malware has been in operation since July 2022. It is a Remote Access Trojan (RAT) that initially targeted outdated network edge devices but has since expanded to include various organisations in Taiwan and even reconnaissance against a US government server. The malware has been actively scanning for vulnerabilities in web cameras and DVRs, particularly those of Chinese origin.
APT34 malware is said to have originated from Iran, and its first occurrence was observed in the year 2014. China-originated K4spreader malware's first occurrence was identified in the year 2024. FlightNight Malware and Hamster Kombat Malware are visible as new cyber threats in the year 2024. Since 2023, SharpRhino malware has been identified as active. While many malware's origin and first occurrence were not clearly known, DarkGate malware has existed since 2018, Nova Snake malware since 2020, perfctl malware since 2021, SystemBC malware since 2019, and TheMoon malware since 2014.
In 2024, few malware attacks were more visible in global cyber news; the diagram shows more analysis on how those work.
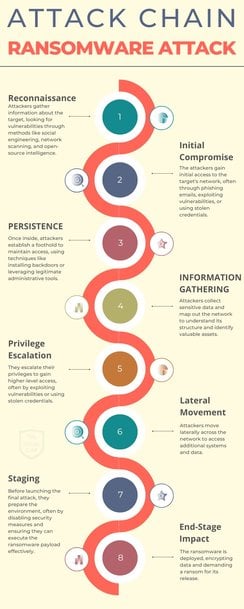
Overview of Ransomware Attacks
A ransomware attack is a type of cyberattack where malicious software, known as ransomware, encrypts or locks a victim's data or device. The attacker then demands a ransom payment to restore access. Ransomware attacks typically follow a series of eight stages, often referred to as the ‘attack chain’.
It has been a very popular cyber attack for years. There are hundreds of such cybercriminal gangs active globally, and many of the ransomwares are named with the gang's name. While many ransomware gangs are underground and it is difficult to find their location or how long they are active in the market, few appear in cyber-news, which can be assumed since then they are visible. APT73 Ransomware and Arcus Media Ransomware were visible in the year 2024. Since 2023, 3AM Ransomware, Abyss Ransomware, Akira Ransomware, BlackSuit Ransomware, and Cactus Ransomware were observed active globally. 8Base Ransomware, Black Basta Ransomware, Black Basta, Bl00dy Ransomware, Daixin Ransomware, Lockbit 3.0 Ransomware, Play Ransomware, RansomHouse Ransomware, and Stormous Ransomware were seen as first occurrences in the year 2022. Since 2021, Avos Locker Ransomware, BlackCat Ransomware, Hive Ransomware, Mallox Ransomware, and Medusa Ransomware were seen as new groups in global cyberattack news. RansomExx Ransomware has existed since 2020, and LockBit Ransomware has been active since 2019.
Earlier ransomware attacks were only doing encryption of the victim systems or data, and they were demanding ransom for the decryption key. If the victim has a backup of the system or data, it was easily restored back to normal. Then ransomware gangs improved their methodologies, starting double and triple extortion techniques. In double extortion, attackers not only encrypt data but also take a backup of it before encryption. Then they threaten to leak it online on the dark web or other platforms. Hence, only having a backup ready to restore doesn't help the victim. Further, in the case of triple extortion, attackers use stolen data to target the victim's customers or business partners by performing DDoS kinds of attacks. Ransomware attacks can be costly, with average costs reaching millions of dollars, excluding ransom payments. They are a significant threat due to their speed and the difficulty in tracing the attackers.
Many cybercriminal gangs are nation-state sponsored as well. Ransomware attacks are increasingly targeting critical infrastructure, including energy, healthcare, and manufacturing sectors. Conflicts between nations like Ukraine, Israel, and the South China Sea have fueled this trend. Factories and industrial facilities, relying on digital transformation, are prime targets. Traditional security methods are often insufficient. Ransomware attacks can disrupt economies, create political instability, and weaken adversaries' infrastructure. International initiatives and legal instruments are being developed to address this threat, improving cybersecurity standards and fostering international cooperation.
Actions Taken Against Cyber Criminal Gangs
In 2024, the FBI made significant strides in combating ransomware gangs. They conducted over 30 disruption operations targeting the infrastructure used by these groups. One notable operation, ‘Operation Cronos’, involved international cooperation to disrupt the notorious LockBit ransomware gang.
In December 2024, Raccoon Stealer malware operator got 5 years in prison after a guilty plea.
How can an organisation be more cybersecure and cyber-resilient?
Below are a few recommendations for the organisations to improve their cybersecurity posture.
Adopt a Defense-in-Depth Mechanism: As more sophisticated cyber attacks have increased in many industry segments, just a couple of cybersecurity controls will not help. Organisations need to identify their mission-critical assets and need to adopt cybersecurity for various layers like data, application, host or endpoint, network, and physical perimeter, and then the overall governance cybersecurity layer.
There are many cybersecurity standards and frameworks available in the market helping in the structured implementation of the controls. American NIST and ISO 27001 (ISMS) are more popular in the world. Also, it is important to understand that 90% of the business population, which are small and medium businesses (SMBs), globally contribute to maximum employment and high value in GDP. In countries like India, SMBs are known as Micro, Small, and Medium Enterprises (MSMEs). In a few countries these organisations are also known as small and medium enterprises (SMEs). To reduce the cyberattack surface, these organisations can even adopt the Business Domain-Specific Least Cybersecurity Controls Implementation (BDSLCCI) framework, which is cost-effective, easy, and tailored to their business domain.
Cyberattacks often stem from inadequate employee cybersecurity awareness. Effective training should cover phishing precautions, policies, and insider threats, with employee testing for effectiveness.
Beware of Supply Chain Attacks: Third-party users, access to vendors and external applications should be monitored.
Monitor Your Network: Regularly monitoring network logs and business transaction notifications is crucial for detecting malicious activities and taking necessary action to prevent them.
Regular Security Audits: It is important to perform vulnerability assessment and penetration testing (VAPT) for the various IT assets of the organisation, which should be part of the governance process, with processes enhanced as needed and compliance improved.
Incident Handling Process is Must: Organisations need to be ready with a working plan for the unseen cyber incident. They need to track incidents as a report until permanent closure. Also, organisations need to prepare a business continuity plan (BCP) for any unseen circumstances, including natural disasters and cybercrimes.
Hope this article will help many organisations to understand the importance of cybersecurity controls implementation to protect their business, reputation, finance, and growth in the new year.
About the author
Dr Shekhar Pawar is a DBA in the cybersecurity domain at SSBM Geneva, Switzerland. He has completed his executive management degree from SJMSOM, IIT Bombay, and engineering in electronics and telecommunications from Mumbai University. Some of his skills and certifications include Certified Information Systems Auditor (CISA), Certified Ethical Hacker (CEH), Computer Hacking Forensic Investigator (CHFI), ISO 27001 – Lead Auditor, PCI DSS Implementer, Certified HIPAA Compliance Professional, Sarbanes Oxley (SOX) Certified Professional, Diploma in Cyber Laws, Microsoft Certified Professional (MCP), Certified Blockchain Developer, Certified ATM for CMMi Assessment, DSP & Applications – IIT Madras, and Diploma in Industrial Electronics. He is also the author of the nonfiction book ‘Air Team Theory: Understanding 10 Types of Teammates and Best Practices to Succeed’. Currently, he is working as Founder and CEO of SecureClaw Inc., USA, and GrassDew IT Solutions Pvt Ltd, Mumbai.

